PG Nibbles
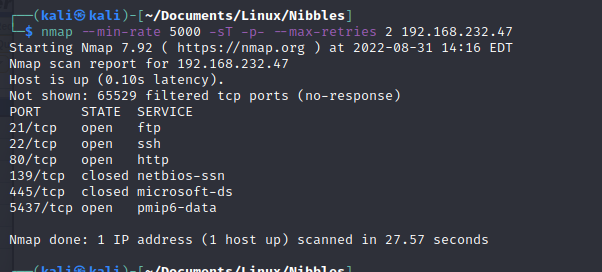
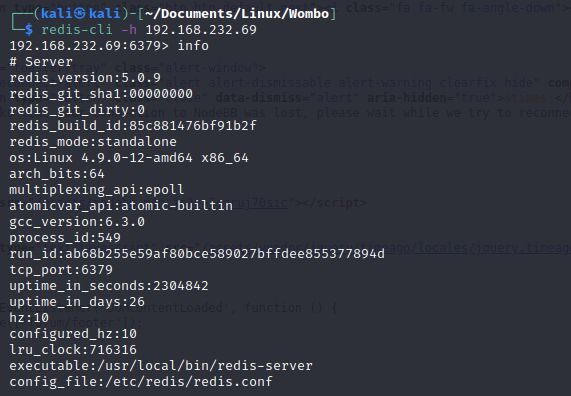
I look into vsftpd 3.0.3 first. Only a DDoS vulnerablity exists. Anonymous login is not working. I move onto port 80. I don't see anyting interesting. ffuf is not showing anything. It must be the postgresql server. I try psql and it does not work. It does not work because I need to set the port! The postgresql is sitting on port 5437 . The default port is 5432 . The default username/password is postgres/postgres. I don't know much about postgres so I go on hacktricks. https://book.hacktricks.xyz/network-services-pentesting/pentesting-postgresql The three metasploit modules stand out. I read the /etc/passwd file. wilson is a user. I try to read /home/wilson/.ssh/authorized_keys and /home/wilson/.ssh/id_rsa. He does not have either. Reading doesn't help. The /bin/bash on postgres is insteresting to me. I got stuck on this part for 1 hour. I use my favorite port 443 for reverse shells. Most Firewalls allow port 80 and 443. In Offsec fashion, they