FristiLeaks 1.3
Information:
Name: FristiLeaks 1.3
VM Creator: @Ar0xA
Time it took me: 8-10 hours.
Rating: 8/10. Its rated as "Basic" but its harder than basic imo. If you have little to no experience with privilege escalation, this one will take you a few hours. In the VM description it said 'box should take like 4 hours. Yeah... not me.
Recommend: Yep.
$ nmap -A -p 0-65535 192.168.0.5
80/tcp open http Apache httpd 2.2.15 ((CentOS) DAV/2 PHP/5.3.3)
| http-methods:
|_ Potentially risky methods: TRACE
| http-robots.txt: 3 disallowed entries
|_/cola /sisi /beer
|_http-server-header: Apache/2.2.15 (CentOS) DAV/2 PHP/5.3.3
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
Port 80 is the only service up. This scares me a bit since I usually use SSH or FTP to login remotely. When I was in the box I seriously tried to do (service sshd start), (service ftpd start) as a low privileged user. I found out you need sudo access to start a service below port 1024. I tried to go into /etc/sshd/config and change the port, but root owned the file. I didn't have the privilege to change anything.
I visit the webpage and guess http://192.168.0.5/fristi is a directory. The "fristi" word is not something you'll find in raft-large-directories.txt. Sine /cola and /beer were disallowed, I thought fristi might exist.
TODO:
We need to clean this up for production. I left some junk in here to make testing easier.
- by eezeepz
I tried "eezeepz:keKkeKKeKKeKkEkkEk" and logged in successfully. PS: not a fan of the username eezeepz. Memory of typing that is not good. So after that your left with an upload button. You need to rename the file as a .png, .jpg file or it'll yell at you. I uploaded php-reverse-shell.php.jpg and ws0.php.jpg.
I am used to reverse webshells but not bind ones. I was getting annoyed with the double text output and thought WSO.php might solve my issues. It did not. I like WSO.php. The little part where you could connect via port 131337 (or set it up) was a cool feature.
Currently we are the apache user. I find notes.txt in the /var/www directory. Here's what it says:
hey eezeepz your homedir is a mess, go clean it up, just dont delete
the important stuff.
-jerry
Okay. Lets go visit /home/eezeepz. We find another notes.txt.
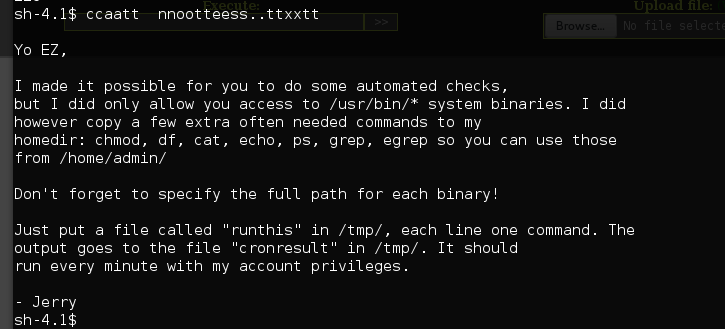
It says if we go in /tmp, make a file called runthis, we will run commands via the admin user. Also make sure to spawn a /bin/bash for your apache user. python -c 'import pty; pty.spawn("/bin/bash")'
 I chmod 777 the whole /home/admin directory to make things easier for me. whoisyourgodnow.txt and cryptedpass.txt each have passwords in them. We need to decipher what they actually are. Lets look at the cryptedpass.py script:
I chmod 777 the whole /home/admin directory to make things easier for me. whoisyourgodnow.txt and cryptedpass.txt each have passwords in them. We need to decipher what they actually are. Lets look at the cryptedpass.py script:
#Enhanced with thanks to Dinesh Singh Sikawar @LinkedIn
import base64,codecs,sys
def encodeString(str):
base64string= base64.b64encode(str)
return codecs.encode(base64string[::-1], 'rot13')
cryptoResult=encodeString(sys.argv[1])
print cryptoResult
We have to work our way backwards. Do this: 1. ROT13 the string.
2. Reverse the string.
3. Base64 decode the string.
Start: =RFn0AKnlMHMPIzpyuTI0ITG
fristigod:LetThereBeFristi!
Start: mVGZ3O3omkJLmy2pcuTq
admin:thisisalsopw123
Do a su fristigod and input the password. Do a sudo -l and see what permissions you have.
You notice you can run /var/fristigod/.secret_admin_stuff/doCom as sudo. Go over there and see what it does.







Comments
Post a Comment