Rickdiculously-Easy Walkthrough
Information:
Name: Rickdiculously-Easy (Rick and Morty themed VM)Link: https://www.vulnhub.com/entry/rickdiculouslyeasy-1,207/
VM Creator: Luke
Time it took me: 3 days to solve it. Around 6-10 hours.
Pentest Skill Level: Less than a year.
To begin use nmap. Note: I lost a few hours by not scanning with -p 0-65535.
$ nmap -A -p 0-65535 192.168.0.6
Starting Nmap 7.01 ( https://nmap.org )
Nmap scan report for 192.168.0.6
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh
80/tcp open http Apache httpd 2.4.27
9090/tcp open zeus-admin ssl/zeus-admin?
13337/tcp open unknown
22222/tcp open unknown OpenSSH 7.5 (protocol 2.0)
60000/tcp open unknownI will go after 80 first. I type in http://192.168.0.6/robots.txt into the browser.
The root_shell.cgi is a trap. Rick wouldn't make it that easy. The /cgi-bin/tracertool.cgi is what were after. The traceroute program takes an IP and does a traceroute command on it. Lets see if we can inject data into the URL. Whoops! It looks like the cat command shows a cat. I found out I can run echo, whoami, pwd, and ls. We are currently the apache user. I'm interested in the /etc/passwd file so we know who the users are. I suspect echo can still print out file contents. We find out Summer, Morty, and RickSanchez are user accounts. Next we will look for existing directories. I use dirb and fuzzdb (https://github.com/fuzzdb-project/fuzzdb) wordlists.
$ dirb http://192.168.0.6 -w raft-medium-directories.txt
---- Scanning URL: http://192.168.0.6/ ----
+ http://192.168.0.6/cgi-bin/ (CODE:403|SIZE:217)
+ http://192.168.0.6/index.html (CODE:200|SIZE:326)
==> DIRECTORY: http://192.168.0.6/passwords/
+ http://192.168.0.6/robots.txt (CODE:200|SIZE:126)passwords looks like an interesting directory. Once we go there we get a flag: FLAG{Yeah d- just don't do it.} - 10 Points. There is also a password.html file waiting for us. Lets check out the source code.
You can probably connect the dots of who owns the password winter. Lets SSH into Summers account. We know there is a SSH service on port 22222.
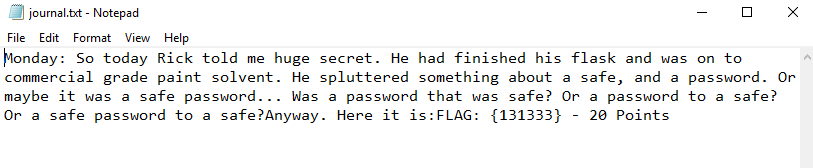
ssh -p 22222 Summer@192.168.0.6It worked! There is a FLAG.txt inside of Summer's home directory. FLAG{Get off the high road Summer!} - 10 Points. Since Morty is dumber than Rick (easy target), lets visit his directory to see what he has. Morty has two files. One called SafePassword.jpg and another called journal.txt.zip. Lets open up SafePassword.jpg in Notepad++.
The journal.txt.zip is a password protected file. We found the password Meeseek. Lets try it out. The Meeseek password worked. Morty gave us a clue about Rick. We have the code 131333 and need to do something with it. Lets visit /home/RickSanchez. There is a file called "safe". We can't run it. Use the cp command and copy the file into Summers home directory. Note: I lost so much time here. I scp the file to my kali box. Since it had something about "cbc-rijndael-128" in the binary, I thought I had to decrypt the file. I was using
openssl enc -aes-128-cbc -d -in safe -out safe.txt -k $i openssl to decrypt the file. I was getting "bad magic number" and thought it was part of the program. Since Morty isn't the brightest, I thought he misheard the safe code. I ran my bash script all night and was left with "bad magic number" and no solutions. I read up on ELF files and realized you can execute them like so ./safe. As long as you have the right libraries installed.
Rick gives us a clue that the password will include one uppercase character, one digit, and a word from his past band name. This sounds easy. I use Java to make a wordlist.
Since I'm lazy, I'll just use hydra to brute-force RickSanchez. I tried to bruteforce SSH multiple times and received no matches. I tried my luck with FTP instead.
We find out the RickSanchez password is P7Curtains. We do a sudo -i and we have root access!Miscellaneous Flags:
1. Visit: https://192.168.0.6:9090. FLAG {There is no Zeus, in your face!} - 10 Points
2. Login as anonymous:anonymous on FTP. FLAG{Whoa this is unexpected} - 10 Points
3. nc 192.168.0.6 60000. FLAG{Flip the pickle Morty!} - 10 Points
4. nc 192.168.0.6 13337 FLAG:{TheyFoundMyBackDoorMorty}-10Points
There is a total of 130 Points or 9 flags.












Comments
Post a Comment