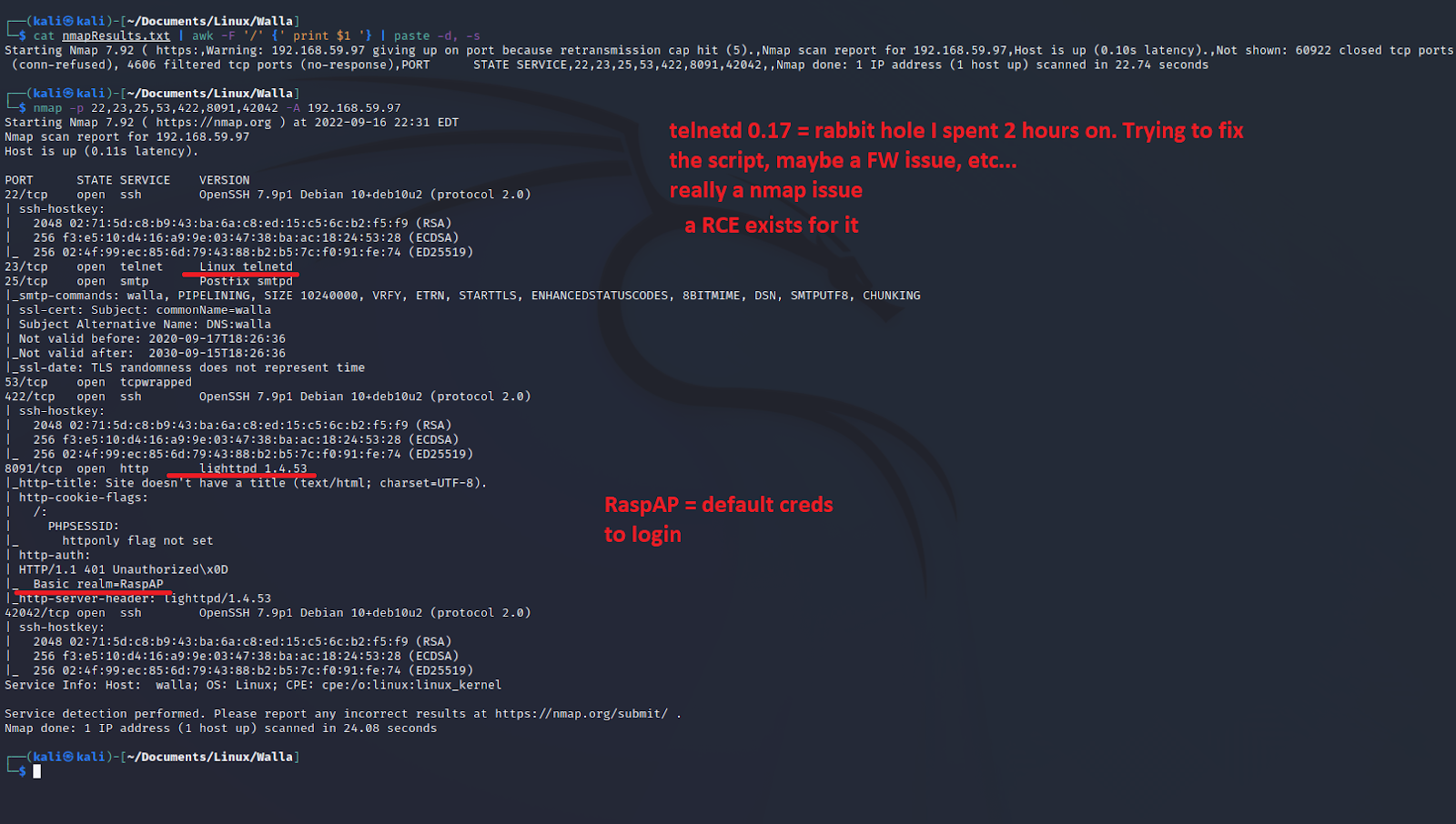
RPC: It's Actually Useful Jutsu

Where have I seen RPC be useful? Need to collect usernames to brute-force. Request a TGS-Ticket by username ONLY: AS-REP Kerberoasting A password was left in the AD User Description https://www.hackingarticles.in/active-directory-enumeration-rpcclient/ 1. Login with RPC rpcclient -U "" -N 10.10.10.161 1. enumdomusers 2. queryuser queryuser svc-alfresco 3. enumdomgroups and querygroup enumdomgroups querygroup 0x200 querygroupmem 0x200 (get the group member IDs) 4. Get Password Info rpcclient $> getdompwinfo min_password_length: 7 password_properties: 0x00000000 5. Create a User (Need priv) createdomuser hacker setuserinfo2 hacker 24 Password@1 enumdomusers