PG Mice
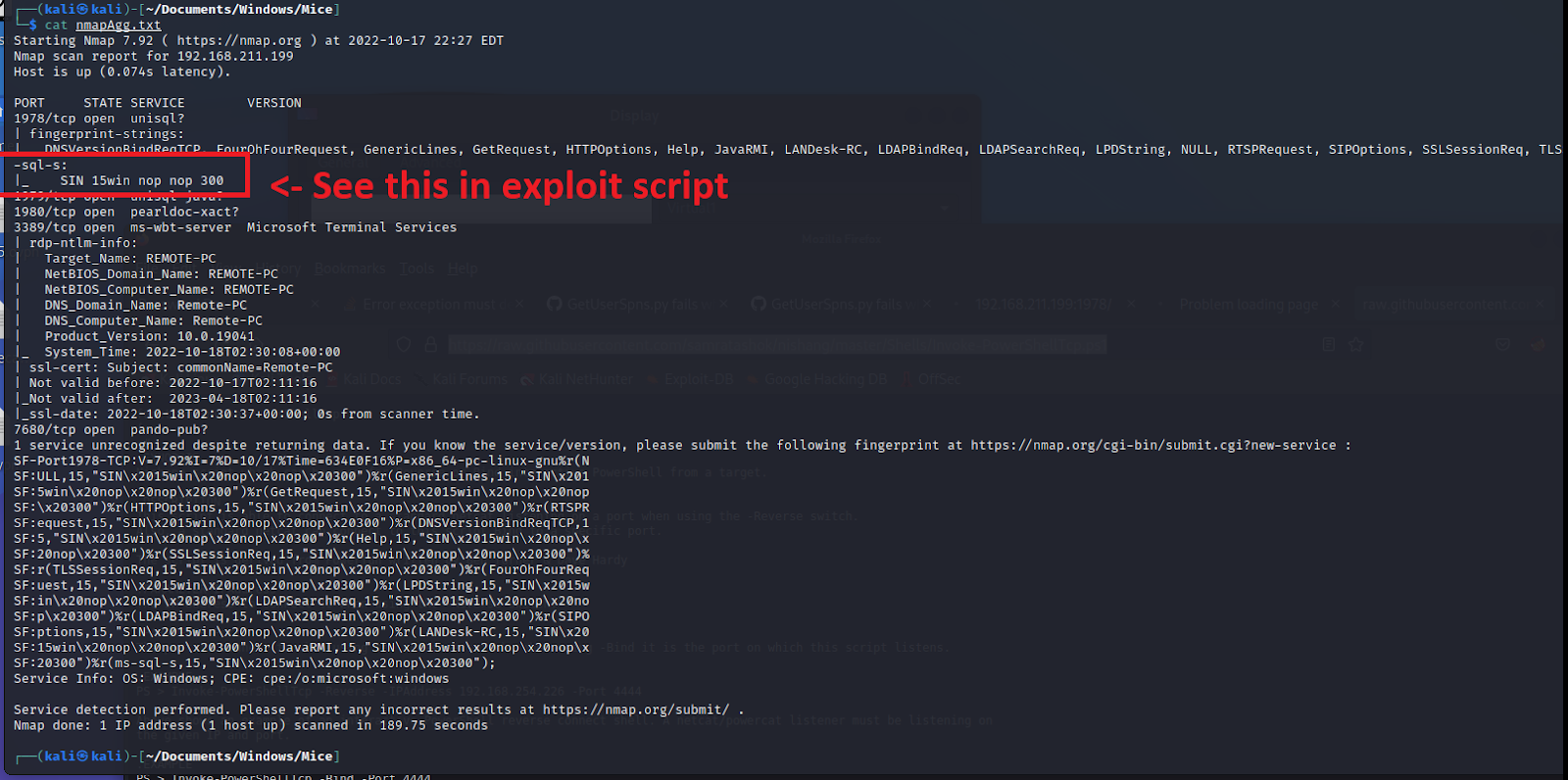
I haven't seen these ports before. The agressive nmap scan doesn't give much information. I google the 1978 port.
Since the box is called "Mice" and the exploit is called "RemoteMouse", it tips me off. I look into the exploit and see the SIN 15WIN NOP NOP text. This must be it.
I edit the script and realize the issues are because this is python2. I run python2 expoit.py and it works. I download a faster exploit script too.
I try multiple reverse shells and fail. I throw my hands up and do the "Give Up! Download netcat and use that instead!" step. I get shell on the box.




Comments
Post a Comment