HTB Traverxec
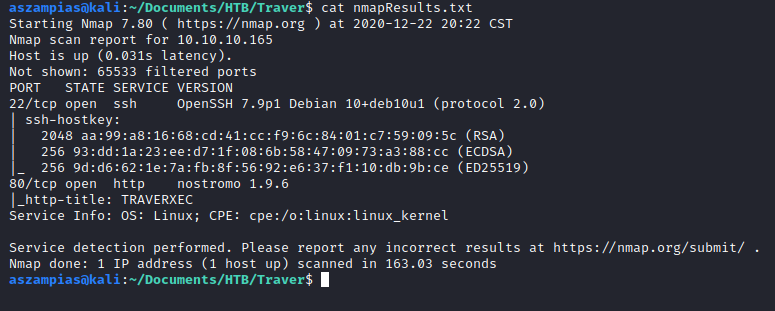
Lessons Learned If user directories are hosted on a website, the usual syntax is /~amanda Minimize a window for priv esc is an attack. Ippsec stty method After doing a nmap scan, we see port 22 and 80 is open. Looking around the website, I see the banner nostromo 1.9.6. Thats different than the usual Apache or Nginx. I look it up in SearchSploit and see a Remote Code Exectuion exploit exists. Ippsec method for better shell: -- Gives you tab autocomplete -- CTRL Z stty raw -echo Type fg ENTER, HIT it TWICE -- Gives you tab autocomplete -- export TERM=xterm (now you can clear the screen) I run linpeas and see it highlighted the /var/nostromo/conf/.htpasswd file that contains "david:$1$e7NfNpNi$A6nCwOTqrNR2oDuIKirRZ/" The hash matches format 500. I will use that in hashcat. Strange Priv Esc /usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service Run the command up above. Minimize your terminal window. . This will bring ...